DKIM (DomainKeys Identified Mail) is used to verify that the content of an email is trustworthy, meaning the content has not been changed from the time the email was transmitted by the sending mail server.
This additional layer of trust is established using a standard public/private encryption key signing process.
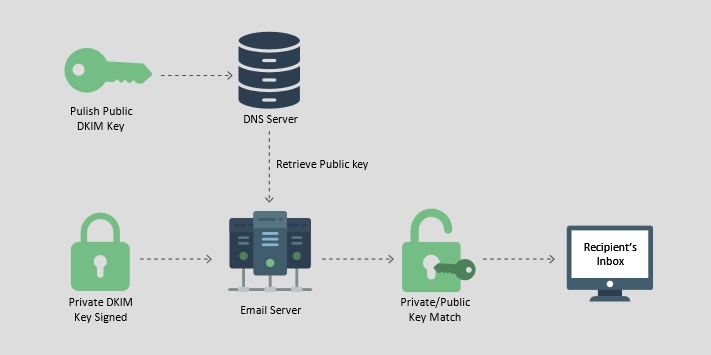
The domain owners must add a DNS entry for their email server and include their public DKIM key. The DKIM key can be used by receivers to verify that the DKIM message signature is correct. For the sender, the email server signs the emails with the corresponding private key.
This diagram shows how the DKIM process works, from the DKIM Key’s all the way to the Intended recipient’s inbox.
DKIM will not stop all malicious actors from attempting to use your domain to send email. The Recipients mail server must be setup to perform sender authentication checks, thereby allowing them to screen clearly fraudulent email.